Active Directory Search Using the Windows User Interface - dsquery
This post intends to document different methods for a standard, non-privileged user who is logged in a domain-joined computer to browse the Active Directory schema, list Active Directory domains, shares and objects as well as perform various searches. This is possible by levaraging native Windows functionality. Leveraging native functionality, also referred to as Living Off The Land (LOTL), helps attackers evade detection more effectively. The available information can be valuable to anyone that perfoms reconnaissance in an AD domain.
The post is divided in the following sections:
- Introduction
- Active Directory Search Using File Effective Access
- Search Active Directory Functionality in the Network Folder
- Forensic Artifacts
- References
Introduction
In security assessments of digital infrastructure configured with Windows operating systems, security professionals who are asked to assess the security posture of an estate are often given access to a Windows host (physical or virtual) that has limited functionality and usually increased defenses. Often it is not possible to run any publicly available tooling. In these moments professionals rely on native Windows functionality.
Thankfully, the Windows operating system offers native funtionality that allows users to retreive information related to the Active Directory. This post lists methods that would allow a user of the Windows operating system to query AD and retrieve information related to users, groups and computers.
How this legitimate functionality can be leveraged by users with malicious intent who are after your estate, you may be wondering. The answer is that the information that can be retrieved with this functionality includes (and is certainly not limited to):
- The list of domain user, computer & group objects, that can provide insight on what accounts are enabled or disabled as well as what users or key systems will further be targeted.
- The list of domains that exist within the environment, which can assist in identification of legacy domains for example.
- User account credentials within the description attribute of user objects that can assist in lateral movement.
- Home folder of user accounts that may point to additonal network file shares and therefore lead to the discovery of additional file shares in the AD environment.
- List of accounts that do not require a password.
All these - combined or not - could allow for further exploitation.
The methods discussed in this post are publicly known and have been mentioned publicly on the internet [1], [6].
Active Directory Search Using File Effective Access
Users are allowed to perform “Common Queries” on AD by leveraging the advanced functionality presented on the window “Select User, Computer, Service Account, or Group” that opens when a user clicks on the options “Select a user” or “Select a device” on the “Effective Access” tab of the Advanced Security Settings (Security tab) when inspecting the “Security” tab on the properties of a file. The window that allows the search is presented below. A clear path describing how the user can reach the functionality follows the image.
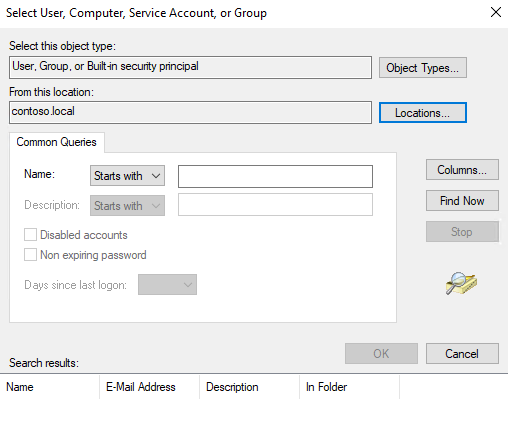
To arrive to the above window, a user has to do the following actions:
- Right click on a file and click the “Properties” on the context menu.
- Navigate to the “Security” tab and click the “Advanced” button to review special permissions or advanced settings of the file, locate at the bottom right.
- On the “Advanced Security Settings” window that opens, navigate to the “Effective Access” tab.
- Click on “Select a user” or “Select a device” links.
- Congratulations! You have arrived on the “Select User, Computer, Service Account, or Group” window.
- Click on the “Advanced…” button located at the bottom left corner of this window to open a (little) more advance functionality.
Users can include additional columns by hitting the “Columns…” button and perform searches hitting the “Find Now” button. Although this functionality is very limited, it is still useful when any other tooling is not available.
Risk Remediation
NoSecurityTab
As long as this functionality is available through the Security tab of files, which also enables users to change the security settings or view a list of users that have access to the reviewed files, one option to restrict this is to disable the Security tab. This can be configured with the group policy documented by Microsoft in [7]. The setting is also documented in [8].
In the Group Policy Editor the setting Remove Security Tab is located in User Configuration -> Administrative Templates -> Windows Components -> File Explorer.
Search Active Directory Functionality in the Network Folder
Intro
This functionality is not as limited as the one described earlier and in fact, allows users to retrieve information from Active Directory for the following:
- Users, Contacts, and Groups
- Computers
- Printers
- Shared Folders
- Organizational Units
- Custom Search
- Common Queries
Each of the above options (excuding the Common Queries) offer additional “advanced” functionality with which a user can add certain criteria in their searches, providing additional flexibility. The “Custom Search” option specifically allows searches using raw LDAP queries. Correct, you can perform LDAP queries using the operating system’s window interface. The downside of this approach is that the search results can only be reviewed on the windos they are printed on and therefore they cannot be exported for further processing.
Something to consider across different operating systems is that users must navigate through a different route to arrive to the described functionality. Therefore, this functionality is dependent on the operating system used.
This is a short index of the operating systems covered later in this post:
The search functionality can also be enabled using the command line listed below. This is an operating system-agnostic command line that only requires the presence of the library dsquery.dll on the host.
rundll32 dsquery,OpenQueryWindow
Windows 10
The “Search Active Directory” funtionality is located in the “Network” ribbon of the Network folder (also known as Network locations). To arrive there, open a file explorer window and click on the Network folder located in the left hand-side pane. The following image shows the “Search Active Directory” button:
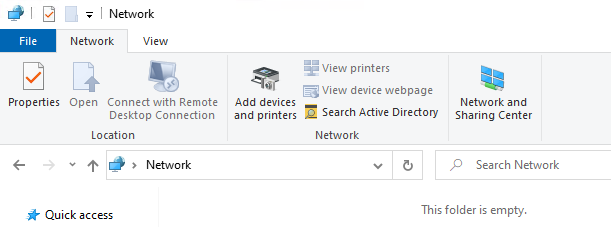
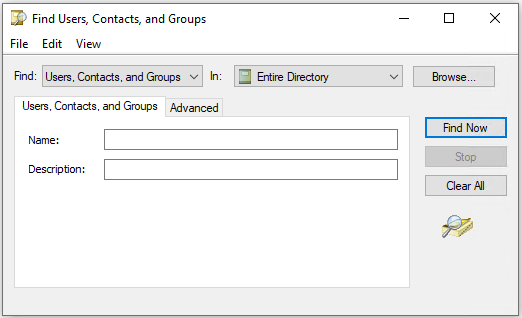
As soon as the button is clicked, the following window opens:
Windows 11
On Windows 11 due to the changes in the user interface, the button is not located in the Network folder. However, it still possible to locate the button that is located in the older interface. To open the older interface type “Windows Tools” in the task bar search and open the suggested application. The older interface (same as the interface Windows 10 use) and click on the Network folder.
Risk Remediation
It would be irresponsible to only underscore the potential risk without including how this feature can be limited. Browsing the internet as part of this research, two possible methods of restricting this functionality on hosts were identified. Restricting using:
The effectiveness of these remediation methods has not been tested as part of this research. Furthermore, the Group Policy setting may be implementing similar configuration with the one described in the Registry Key section.
Group Policy Object
The information presented in this section was retrieved from [2].
The group policy that governs the “Search Active Directory” button is located in the tree structure User Configuration\Administrative Templates\Desktop\Active.
The three settings that exist in that path, are:
Enable filter in Final dialog boxHide Active Directory folderMaximum size of Active Directory searches
The setting that disables the button in the window ribbon is Hide Active Directory folder. However, per Microsoft, the hide functionality is only supported on Windows 2000 systems and therefore it seems a legacy setting. What this functionality does under the hood, is detailed in [3]. Effectively, it sets the value HideDirectoryFolder of the registry key HKEY_CURRENT_USER\Software\Policies\Microsoft\Windows\Directory UI to 1. Further research revealed that Microsoft has incorporated these settings in Configuration Service Providers (CSP), which are detailed [4] and cover the Windows 10 and Windows 11 operating systems.
Alternatively, in newer versions of Windows the setting Maximum size of Active Directory searches can be set to 0. Effectively, this setting hardens the functionality and returns 0 results.
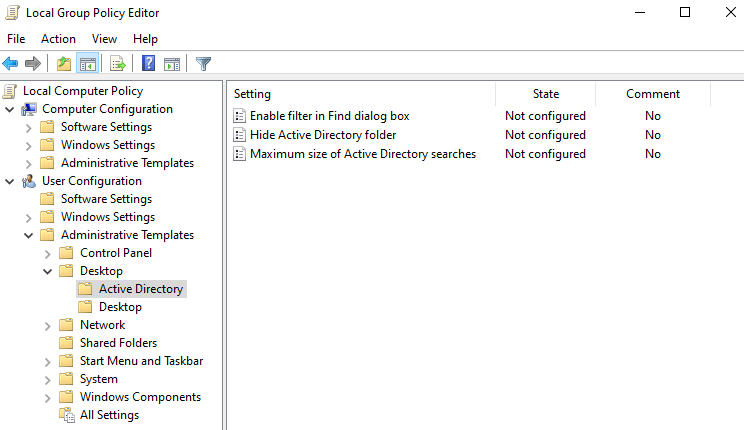
There is pretty much a policy setting for everything on Windows. The challenging task is to locate it, understand its purpose and finally test and implement the configuration.
Registry Key
The information presented in this section was retrieved from [5].
To remove the “Search Active Directory” button from the Network window ribbon, users can locate the relevant key in registry and delete it. In more detail:
- Set a Group Policy Security Setting – Computer Configuration/Policies/Windows Settings/Security Settings/Registry – right click and Add Key. Navigate to
HKLM\Software\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.SearchActiveDirectory. - Set Configure this key then Replace existing permissions. Click on Edit Security, then Advanced. Change the Owner to Everyone.
- Set permissions on the key so that CREATOR OWNER, SYSTEM and your domain admins have Full Control.
- Test that the GPO applies these permissions with gpupdate /force on the client.
- Now set a Group Policy Preference – Computer Configuration/Preferences/Windows Settings/Registry – right-click and select New->Registry Item.
- Action: Delete,
hive HKEY_LOCAL_MACHINE, key pathSOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\CommandStore\shell\Windows.SearchActiveDirectory - Run gupdate /force again – the key should disappear.
Caveat: This method may not be the most suitable for production environments and must be tested thouroughly before implementing.
Forensic Artifacts
Registry Keys
Use of dsquery creates registry keys that evidence that relevant functionality has been used. More spefically, on an Active Directory-joined computer, registry keys are created in:
HKEY_USERS\<USER SID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Directory UI\QueryForms
For example, on the dsquery user interface, selecting the form to list computers, the following registry key is created when the serch is performed:
HKEY_USERS\<USER SID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Directory UI\QueryForms\{16006700-87AD-11D0-9140-00AA00C16E65}
The following registry key is created when the ‘Custom Search’ is performed:
HKEY_USERS\<USER SID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Directory UI\QueryForms\{83EE3FE3-57D9-11D0-B932-00A024AB2DBB}
Process Events
The dsquery window is opened with the help of the native windows host process rundll32.exe. Therefore, this process will be the source of LDAP queries to the Domain Controllers of a domain.
Additionally, an attacker may also exploit COM Hijacking by registering their own class identifier (CLSID) to hijack normal dsquery functionality. CLSIDs related to dsquery are listed below.
- {83BC5EC0-6F2A-11d0-A1C4-00AA00C16E65}
- {8A23E65E-31C2-11d0-891C-00A024AB2DBB}
- {1ab4a8c0-6a0b-11d2-ad49-00c04fa31a86}
- {DE4874D2-FEEE-11d1-A0B0-00C04FA31A86}
References
[1] https://serverfault.com/questions/261381/how-to-view-all-users-and-groups-in-ad-without-logging-onto-the-dc
[2] https://www.edugeek.net/forums/windows-7/49603-remove-search-active-directory-windows-7-a.html
[3] https://admx.help/?Category=Windows_10_2016&Policy=Microsoft.Policies.WindowsDesktop::AD_HideDirectoryFolder
[4] https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-desktop
[5] https://welsheduit.wordpress.com/2017/04/28/windows-10-ui-tweaking-ribbon-bar/
[6] https://www.pcreview.co.uk/threads/prevent-domain-users-from-browsing-active-directory-ous.1456319/
[7] https://learn.microsoft.com/en-us/windows/client-management/mdm/policy-csp-admx-windowsexplorer#nosecuritytab
[8] https://admx.help/?Category=Windows_10_2016&Policy=Microsoft.Policies.WindowsExplorer::NoSecurityTab
tags: #active directory