Start Menu to SSH, with a Quick Nip Through SiHost
Parent-child process relationship is always a good starting point for investigations that rely on EDR telemetry. By defining and documenting what exactly is normal behavior, we can make out behavior that diverts from this norm and therefore create investigation leads. This blog investigates what happens under the cover (not very deeply) when you type SSH on the start menu. It may be useful for Incident Response practiotioners and anyone interested in normal (and abnormal) Windows activity. The research was performed on a Windows 10 system.
The post is divided in the following sections:
- The parent process of cmd, PowerShell and PowerShell ISE
- The parent process of SSH
- SiHost or Explorer
- SiHost and CoreShellComServerRegistrar
- References
The parent process of cmd, PowerShell and PowerShell ISE
On the Start Menu of Windows 10 when someone types the name of an appliction they want to run, the operating system suggests results that match that search. Usually the parent process of the application the user was searching for is explorer.exe. This is the case when someone starts cmd.exe, powershell.exe or powershell_ise.exe, for example. The same applies when these processes are started from the Windows Run utility. Last detail to document is that on the Start Menu along the cmd, the PowerShell and the PowerShell ISE icons, the string System is displayed.
The parent process of SSH
OpenSSH for Windows is available on Windows 10 and allows clients to connect to SSH servers via an encrypted channel. When someone searches SSH on the Start Menu, they are presented with this result:
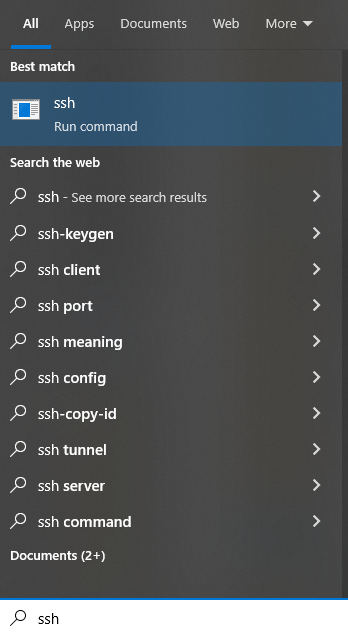
The main difference with what was described earlier, is that Run command is displayed under the SSH, instead of System. Same applies to other OpenSSH utilities, such as sftp.exe and scp.exe. All these, are located in the path C:\Windows\System32\OpenSSH\. Someone would have expected that it wouldn’t have been possible to start these processes without using a command prompt, such as cmd or PowerShell. That’s somewhat correct. If you double click on ssh.exe for example, a command Window gets displayed briefly and then disappears. In other words, the process starts and immediately exits because no arguments are passed to the process.
So, what happens when we pass arguments to ssh.exe directly on the Windows Start Menu? It runs and you get a persistent command Window (subject to what arguments you have provided)! Same behavior occurs when we pass arguments on the Windows Run utility. Obviously, same applies to the other processes of the family (scp.exe and sftp.exe). The difference between these two actions is what process is the parent in each execution method.
SiHost or Explorer
When someone types ssh user@hostname on the Start Menu and hits enter, they are presented with a shell where SSH waits to receive credentials of the user account (if password authentication on the SSH server is allowed). The parent process of ssh.exe in this instance is sihost.exe. The Shell Infrastructure Host executable, in short sihost.exe is a native Windows utility that someone from Microsoft describes as a relay service for various WINDOWS programs in [1].
When SSH is ran with the same arguments (ssh user@hostname) via the Windows Run utility, the behavior is different. The parent process is explorer.exe and not sihost.exe.
So, each parent process would likely indicate a different execution method. Understanding the execution method is critical when answering questions that come up on incident investigations. Context is key!
SiHost and CoreShellComServerRegistrar
Very useful information about sihost.exe is included in Zero Day Initiative’s post [2], which describes that code responsible for the Windows shell environment has been implemented in sihost.exe from explorer.exe. sihost.exe registers itself as a local COM server for various classes. One of them is CoreShellCOMServerRegistrar (associated with CLSID 54E14197-88B0-442F-B9A3-86837061E2FB). This class is implemented in CoreShellExtFramework.dll. The interface implements methods such as OpenProcess. Connecting these pieces together - caveated by my limited knowledge around CoreShellComServerRegistrar, we could say that this is the reason why sihost.exe is the parent process.
References
[1] https://answers.microsoft.com/en-us/windows/forum/all/sihost-is-attempting-to-open-ms-edge/d8f545f2-d0fa-4b89-a4ca-af402e6e1dc6
[2] https://www.zerodayinitiative.com/blog/2019/12/19/privilege-escalation-via-the-core-shell-com-registrar-object
tags: #other