Web Application in Debug Mode Discovery
This post describes how to discover web appications written in specific web application frameworks, by performing surgical searches of key strings. Certain searches reveal web applications that run in debug mode. Error messages displayed in debug mode can reveal the structure of a web application and its additional functionalities, potentially assisting an attacker during reconnaissance operations.
The post is divided in the following sections:
Django
On Django, when requesting a non-existent page from a server that runs a web application in DEBUG mode, the response from the server returns the URL dispatcher [1], known as URLconf, instead of a standard 404 page. Effectively, in Django applications the purpose of the URL dispatcher is to route requests to the appropriate implemented functions. Therefore, by accessing a non-existent page, the web server responds with the URL dispatcher that reveals the structure of the web application. This can assist an attacker in identifying additional web pages or API endpoints that might otherwise remain hidden or unidentified.
Hunting for Django apps
The default 404 page that the DEBUG mode displays, contains certain strings that an attacker could use to search for exposed Django apps that run in DEBUG mode. One of the strings, that is displayed at the bottom of the 404 page, is the following:
You’re seeing this error because you have DEBUG = True in your Django settings file. Change that to False, and Django will display a standard 404 page
Substrings of this, such as True in your Django settings file or your Django settings file could also be searched for on platforms that scan the internet, cache pages and allow searches through a graphical interface or an API to further discover applications in debug mode.
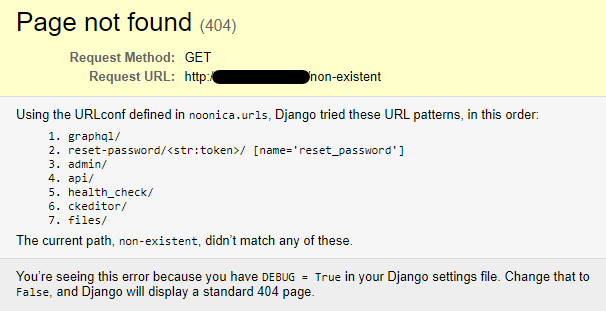
The following image shows the URL dispatcher of a Django application in DEBUG mode found on the internet. To retrieve the URL dispatcher, the request URI that was used was the string non-existent. The page reveals various implemented view functions (in Django terminology).
Rails
On Rails, when requesting a non-existent page from a server that runs a web application in DEBUG mode, the response from the server returns the URL dispatcher, instead of a standard 404 page. Effectively, in Rails applications the purpose of the URL dispatcher is to route requests to the appropriate implemented functions. Therefore, by accessing a non-existent page, the web server responds with the URL dispatcher that reveals the structure of the web application. This can assist an attacker in identifying additional web pages or API endpoints that might otherwise remain hidden or unidentified.
The default 404 page that the DEBUG mode displays, contains certain strings that an attacker could use to search for exposed Rails apps that run in DEBUG mode. One of the strings, that is displayed at the top of the 404 page, is the following:
No route matches
An informative post about the risks of Rails debug mode is located at [2].
Laravel
Stack traces from application developed using Laravel can be identified with the string:
laravel/framework
Remediation
Exposing a development server on the internet is not good practise and introduces security risks. Development environments are usually not sufficiently hardened and lack additional protection layers (such security monitoring software) compared to production environments. To mitigate the risks associated with the exposure of development servers, it is recommended to:
- Take the exposed server off the internet, if the server was exposed unintentionally and additional layers of security have not been implemented. As a stretch, review the available logs to determine if requests have been made from IP addresses other than the ones used by authorized personnel
- If the server needs to remain online on the public internet, configure strict firewall rules that restrict access to only trusted IP addresses
References
[1]: https://docs.djangoproject.com/en/5.0/topics/http/urls/
[2] https://beaglesecurity.com/blog/vulnerability/rails-debug-mode-enabled.html
tags: #reconnaissance